Cyber Security Challenges in the Current Computing Environment
Introduction
The rapid expansion of connected devices through the Internet of Things (IoT) has revolutionized modern society, integrating technology into daily life and critical infrastructure. However, this interconnectedness introduces profound challenges, including cybersecurity vulnerabilities, ethical dilemmas in cyberwar, and the spread of misinformation on digital platforms. Cyber-attacks, such as NotPetya, demonstrate the potential to disrupt economies and societies, while state-sponsored operations like Stuxnet and Pegasus highlight the murky ethics of unrestricted digital warfare. Additionally, digital platforms amplify misinformation by prioritizing engagement-driven content. Emerging technologies, like drones, further complicate the evolving landscape of warfare, necessitating a critical examination of these interconnected challenges.
Definitions
Key terms in the context of connected devices and their challenges include Internet of Things (IoT), referring to the network of interconnected devices communicating data, often vulnerable to cyber threats due to weak security protocols (Mosenia & Jha, 2017). Cybersecurity encompasses measures to protect these devices and networks from unauthorized access or attacks, such as ransomware or DDoS. Cyberwar denotes state or non-state actors using digital tools for strategic disruption, often ethically ambiguous, as seen in cases like Stuxnet (Rid, 2012). Misinformation refers to false or misleading information spread via digital platforms, amplified by algorithms prioritizing user engagement (Bakir & McStay, 2018). Drones are unmanned devices used in modern warfare, reshaping conflict dynamics.
Cyber Security Challenges
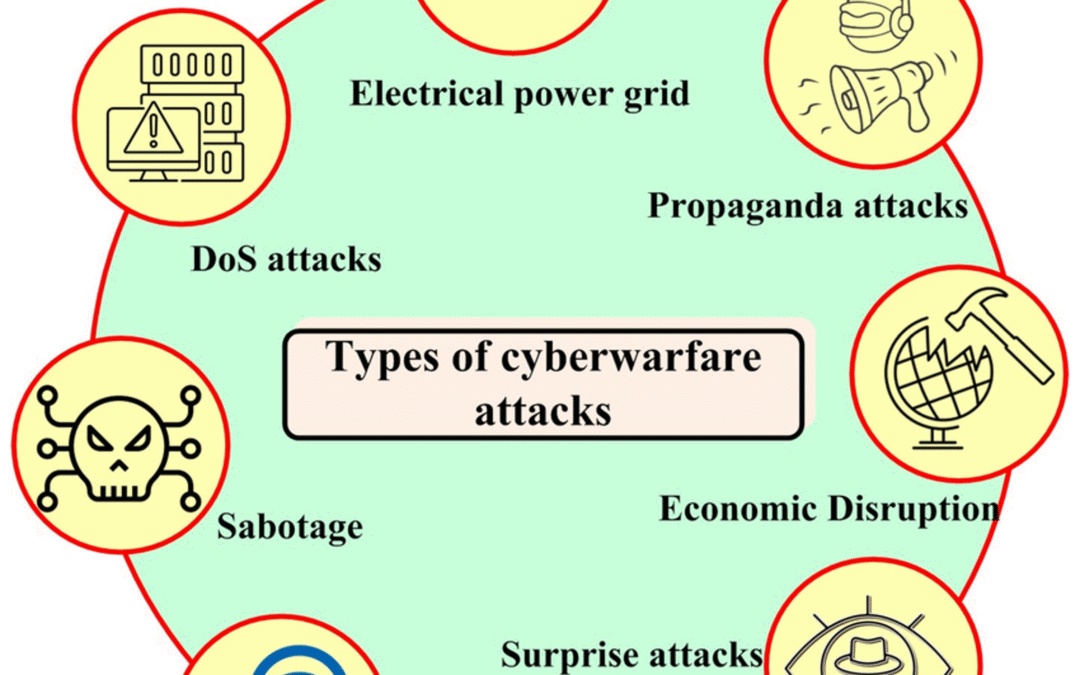
The proliferation of connected devices in the Internet of Things (IoT) has transformed modern society, but it introduces significant cybersecurity challenges. With billions of devices interconnected, from smart home appliances to industrial systems, the attack surface for cyber threats has expanded exponentially. Cybersecurity issues arise from vulnerabilities in device software, weak authentication protocols, and unencrypted communications, making systems susceptible to exploitation (Mosenia & Jha, 2017). Cyber attacks, such as ransomware or distributed denial-of-service (DDoS) attacks, can disrupt critical infrastructure, like power grids or healthcare systems, causing widespread societal havoc. For instance, the 2017 NotPetya attack crippled global supply chains, costing billions in damages and exposing the fragility of interconnected systems. The potential for such attacks to destabilize economies or compromise national security underscores the urgency of robust cybersecurity measures in this hyper-connected environment.
The ethics of cyberwar further complicate this landscape, introducing a paradigm of unrestricted warfare where traditional rules of engagement are murky. Unlike conventional warfare, cyber operations often blur the lines between state and non-state actors, as seen in high-profile cases like Anonymous’ hacktivism or WikiLeaks’ data leaks (Rid, 2012). State-sponsored hacktivists, such as those behind Stuxnet, which targeted Iran’s nuclear program, or Pegasus, used by Israel for surveillance, aim to degrade or disable adversaries’ capabilities covertly. These actions raise ethical questions about proportionality, collateral damage, and accountability in digital warfare. The lack of clear international norms governing cyberwar exacerbates these issues, enabling actors to exploit connected devices for geopolitical gain while evading traditional consequences.
Digital platforms, designed to maximize user engagement, also amplify misinformation, exacerbating societal vulnerabilities. Algorithms prioritizing extreme content can polarize users and spread false narratives, undermining trust in institutions (Bakir & McStay, 2018). Meanwhile, emerging technologies like drones reshape warfare, enabling precise, remote attacks that further blur ethical boundaries. As connected devices proliferate, addressing cybersecurity, ethical cyberwar, and platform-driven misinformation remains critical to safeguarding modern society.
Potential Solutions
Addressing challenges in the connected device ecosystem requires multifaceted solutions. To bolster cybersecurity, implementing standardized, robust encryption and authentication protocols for IoT devices can mitigate vulnerabilities (Mosenia & Jha, 2017). International agreements on cyberwar ethics, defining clear rules for state-sponsored actions, could reduce unrestricted warfare risks, drawing from frameworks like those proposed by Rid (2012). Digital platforms should redesign algorithms to prioritize credible content over sensationalism, curbing misinformation (Bakir & McStay, 2018). For emerging technologies like drones, regulatory frameworks ensuring ethical use in warfare are critical. Collaborative efforts among governments, tech industries, and researchers can foster secure, ethical, and responsible integration of connected devices into society.
Conclusion
Keywords: #Cybersecurity #Cyberwar #Misinformation #Internet_of_Things #IoT #Drones
Image Source: Cavanaugh, S.